The Nobelium group behind the SolarWinds attack allegedly mounted another attack on U.S. government agencies.
What you need to know
- The group behind the SolarWinds attack is allegedly behind another attack on U.S. government agencies.
- Microsoft detected the attack and shared details about it this week.
- The attack used the United States Agency for Internal Development to send out phishing emails to government agencies.
Microsoft observed another attack on U.S. government agencies and shared details about the attack this week. Microsoft identified the group "Nobelium" as the one behind the new email attacks. Nobelium is also the group behind the infamous SolarWinds attacks. Microsoft vice president Tom Burt shares details of the attack in a Microsoft blog post.
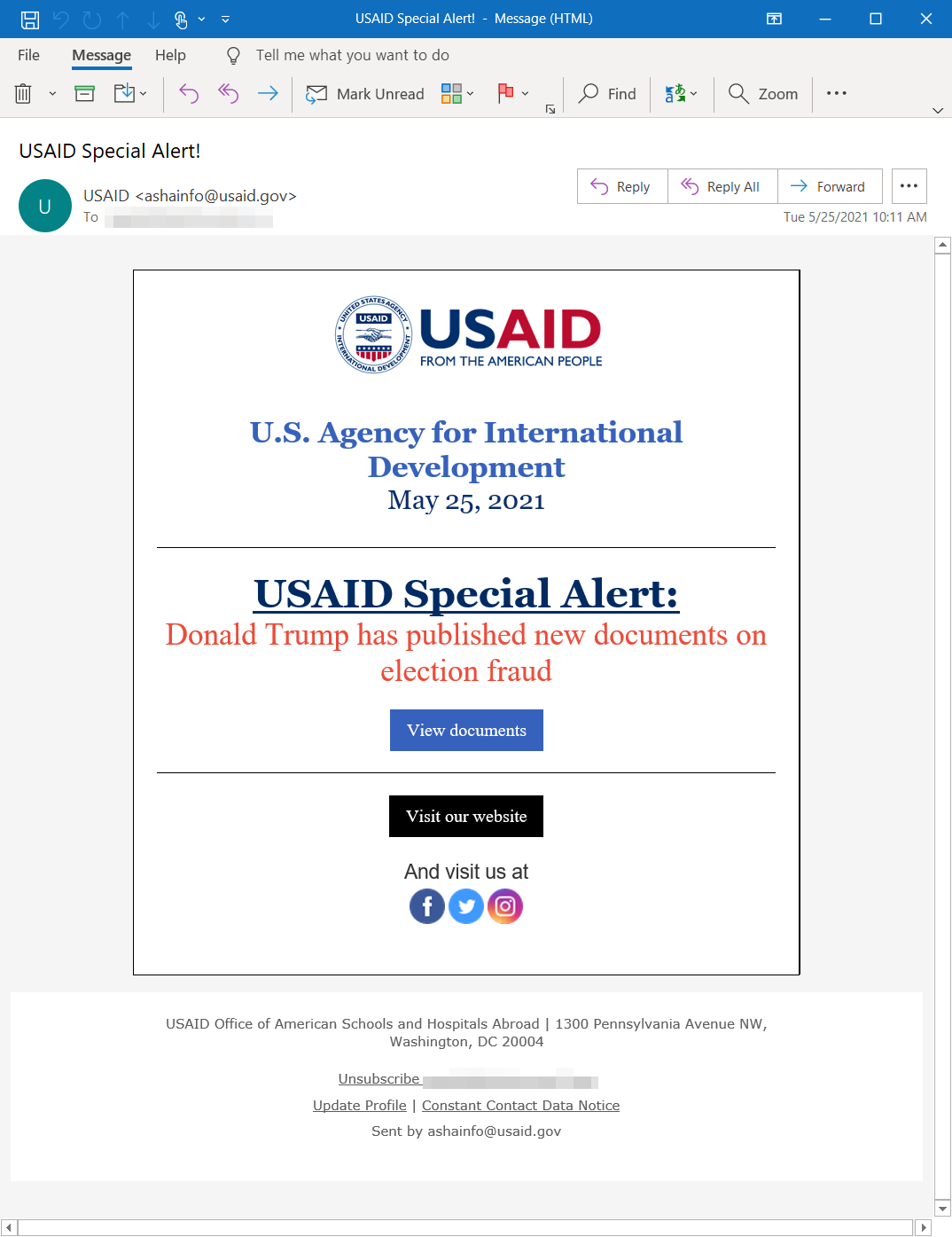
While the attack is allegedly by the same group as the SolarWinds hack, it utilizes a different method. Microsoft reports that Nobelium gained access to the Constant Contact account of the United States Agency for Internal Development (USAID) and sent out approximately 3,000 emails to over 150 organizations.
The phishing emails had a malicious file that would be inserted if a link was clicked in the email. Once the phishing email gained access to a computer, it could be used to steal data from the computer or infect other computers on the same network. Microsoft breaks down the attack in more technical detail in a security blog post.
Microsoft details a specific example of an attack used by Nobelium (via The New York Times). One message sent out in the attack claimed that "Donald Trump has published new documents on election fraud." If people clicked on that link, it would insert malicious files into the computer.
The majority of attack targets are said to be in the U.S., but Microsoft states that at least 24 countries were attacked. At least 25% of the targeted organizations are involved in international development and humanitarian aid, which makes it more likely that people from those agencies would trust an email from the USAID.
Microsoft explains that many of the attacks were blocked by Windows Defender and that it is in the process of notifying customers that have been targeted. The company also states that it has "no reason to believe these attacks involve any exploit against or vulnerability in Microsoft's products or services."
The attacks were first detected on January 25, 2021, though the attacks had not utilized the USAID Contact account on that date. Emails from the USAID account have been sent out as part of the attack as recently as this week. The attack appears to be ongoing, according to Microsoft.
The U.S. government announced several sanctions against Russia following the SolarWinds attack (via The New York Times), which may have affected these new attacks.

No comments: