When CISA speaks up, it's serious.
What you need to know
- The PrintNightmare vulnerability has been leaving machines exposed to outside influence.
- Microsoft has attempted to address the issue via patches.
- CISA has issued a directive to help stop the spread of PrintNightmare's dangers.
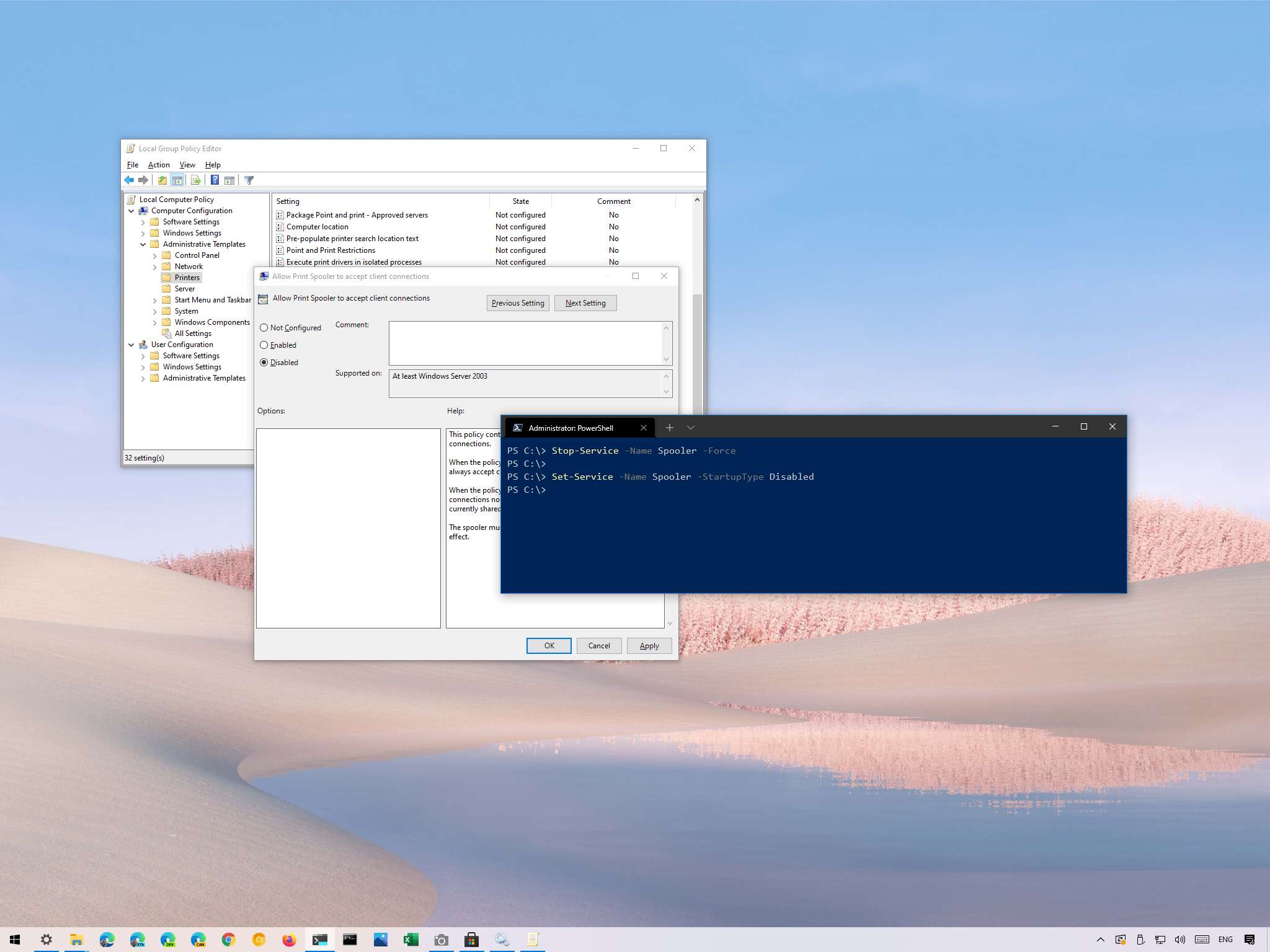
It's all fun and games until the Cybersecurity and Infrastructure Security Agency (CISA) gets involved. If you thought PrintNightmare was a small problem affecting a few people, think again: It's a big enough problem that it's pushed CISA to publish an emergency directive to counter the Microsoft Windows Print Spooler service vulnerability (via Kim Zetter).
Here's a piece of the directive, to give you an idea of what CISA is demanding of all Federal Civilian Executive Branch agencies.
- By 11:59 pm EDT, Wednesday, July 14, 2021, Stop and Disable the Print Spooler service on all Microsoft Active Directory (AD) Domain Controllers (DC).
- By 11:59 pm EDT, Tuesday, July 20, 2021, apply the July 2021 cumulative updates to all Windows Servers and Workstations.
In case you're looking for those cumulative updates yourself, check out our coverage of Windows' July Patch Tuesday. PrintNightmare is addressed in there, so it's worth checking out if you're afraid you're at risk of being compromised.
PrintNightmare is no joke. Attackers who take advantage of the Print Spooler service vulnerability can install programs, view and modify data, and gain user rights by creating accounts on affected machines. Given these consequences, it's no wonder CISA is stepping in to make sure government workers are protecting themselves as much as possible.
To give some perspective on the scope of the issue, another recent time CISA had to get its hands dirty and issue instructions to protect government machines was during the Hafnium-linked Microsoft Exchange Server situation in early 2021.
No comments: